
WhatsApp is a very popular SMS-like messenger for smartphones, but it’s unfortunately only available for smartphones right now. If you want to use other tools or write web applications that send or receive WhatsApp messages (e.g. WhatsAPI, was at https://github.com/venomous0x/WhatsAPI, site now defunct, July 2019), you have to find a way to sniff the WhatsApp password from your smartphone. Until recently, this password was just an MD5 hash of your IMEI (or MAC address), but that has changed when that was uncovered. Since then, the WhatsApp server assigns a password to each device/account when it first registers.
This tutorial demonstrates how to capture the WhatsApp password of your WhatsApp account using the SSL/TLS proxy mitmproxy. Once you have this password, you can use it to communicate with the WhatsApp servers directly or via a framework. This is the first part of a two-part tutorial. The second part demonstrates how to send and receive WhatsApp messages via PHP.
Contents
Updates
- August 2013: I just tried to activate another number from a Samsung Galaxy S3 device with Android 4.1.2 installed. For some reason, WhatsApp traffic is not showing up on neither mitmproxy nor SSLsplit. Although I suspected that the new WhatsApp client is checking the certificate fingerprints (thus making forgery impossible, see github conversation (was at https://github.com/shirioko/MissVenom/issues/7#issuecomment-21899690, site now defunct, July 2019), it might also be an Android issue. I’ll keep you posted.
- October 2013: As suspected in the update above, WhatsApp now checks certificate fingerprints, meaning that other than to change the WhatsApp application itself, I do not see a way to sniff the password. The method described in this post does not work anymore. Also refer to shirioko’s comment (was at: https://github.com/shirioko/MissVenom/issues/7#issuecomment-23489710, site now defunct, July 2019) on the Github discussion.
- December 2013: I kindly ask you to stop e-mailing me about hacking into WhatsApp accounts or sniffing WhatsApp passwords for you. Also, I will not help you to send mass WhatsApp messages – even for money. Thank you!
1. Introduction
1.1. Please note: Linux only tutorial!
Please note that this is a tutorial for Linux users. It uses the TLS/SSL proxy mitmproxy to capture the secure connection between your phone and the WhatsApp servers. If you are a Windows user, please check out MissVenom (was at: https://github.com/shirioko/MissVenom, site now defunct, July 2019), a tool made just to sniff on WhatsApp passwords. All the stuff that’s done with mitmproxy in this tutorial is basically what MissVenom does for Windows users.
1.2. How it works
This tutorial uses a man-in-the-middle attack to intercept the communication between your phone and the WhatsApp servers. To do so, you have to redirect all the traffic from your phone to your Linux machine running mitmproxy (by changing your phone’s default gateway). Mitmproxy, a man-in-the-middle proxy application will then display all of your phone’s HTTP(S) request/responses. While mitmproxy is running, you then need to wipe all of your WhatsApp user data from your phone and set it up as if you were a new user, so that you can sniff into the conversation of your phone and the WhatsApp servers while the WhatsApp account password is exchanged.
Don’t worry. It sounds more complicated than it is and your WhatsApp will just look the same afterwards. Here’s a step-by-step:
- Set up and run mitmproxy and prep you phone (as described in this tutorial)
- Stop WhatsApp and wipe the WhatsApp user data
- Open WhatsApp and re-setup your account
- Sniff the password by monitoring the HTTP(S) traffic
1.3. More about mitmproxy
The tutorial does not include a lot of information about how to set up mitmproxy and what it actually does. If you want to read more, please check out my previous blog post about how to use mitmproxy in general, or of course go to the mitmproxy website and read the manual.
2. Let’s do it!
The following steps correspond to the short step-by-step above. Since I do not have an iPhone, the WhatsApp screens are from the Android version, but it should work equally on an iPhone.
2.1. Set up and run mitmproxy and prep your phone
First you need to set up mitmproxy as described in chapter 2 of the mitmproxy howto. In a nutshell, this tutorial shows you how to enable IP forwarding, set up iptables to redirect all traffic from port 80 and 443 to 8080 as well as how to install and run mitmproxy.
Please note: Explanations on this step are kept to a minimum. Check out the post about mitmproxy to read more.
|
1 2 3 4 5 6 |
sysctl -w net.ipv4.ip_forward=1 iptables -t nat -A PREROUTING -i eth0 -p tcp --dport 80 -j REDIRECT --to-port 8080 iptables -t nat -A PREROUTING -i eth0 -p tcp --dport 443 -j REDIRECT --to-port 8080 apt-get install python-pyasn1 python-flask python-urwid pip install mitmproxy mitmproxy -T --host |
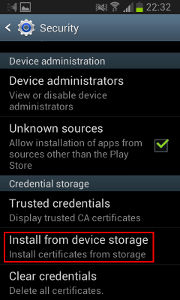
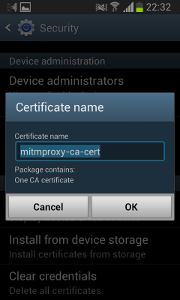
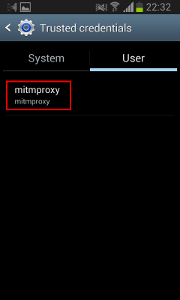
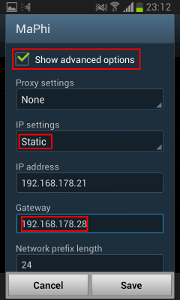
On your phone, you need to install the mitmproxy CA certificate:
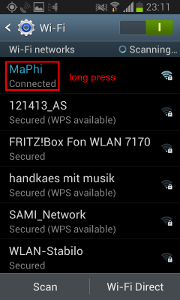
And then change your standard gateway:
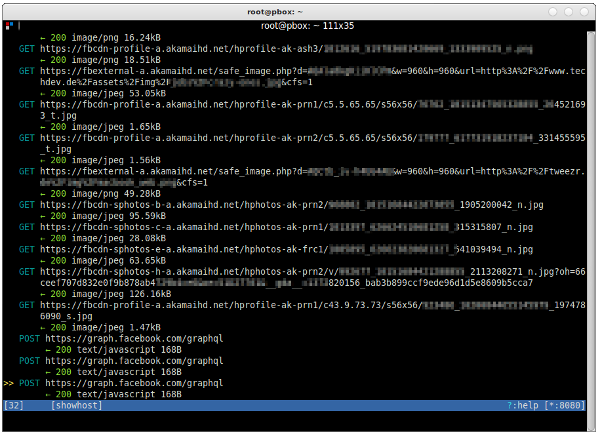
If you’ve done everything correctly, you should be able to see all the traffic that your phone sends, like this:
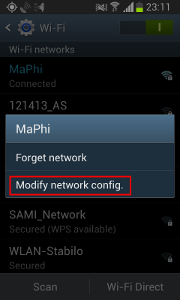
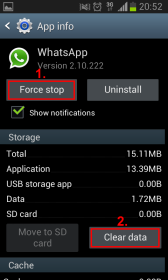
2.2. Close WhatsApp and clear user data
WhatsApp only negotiates a new password with the server when it first communicates with it. If you already have WhatsApp up and running on your iPhone or Android device, you need to wipe the user data, so that WhatsApp can negotiate a new password — which you can then sniff using mitmproxy.
Clearing the existing user data is really simply. Simply go to Settings, Application manager and scroll down to WhatsApp. In the WhatsApp screen, click “Force stop” and then “Clear data”.
And don’t worry, WhatsApp makes a backup copy on its servers and restores all of your messages and conversations once you have re-setup your account. Update August 2013: Please note that according to Adtc’s comment, WhatsApp does not backup the messages on their servers, but on the local device at 4am each night. I have not yet double-checked this, but I just wanted to be sure that you might be losing some older messages.
2.3 Sniff WhatsApp password and restore user data
After wiping all your WhatsApp user data, it’s like you just bought a new phone or reset your smartphone’s operating system. The next time you open WhatsApp, it has to reconnect to your WhatsApp account and exchange a new login password. Given that you now have a sniffer in place and can capture all of your phone’s communication, you can simply read the password off the air.
Make sure mitmproxy is running. Then simply open up WhatsApp and follow the screens:
2.4. Examine mitmproxy results
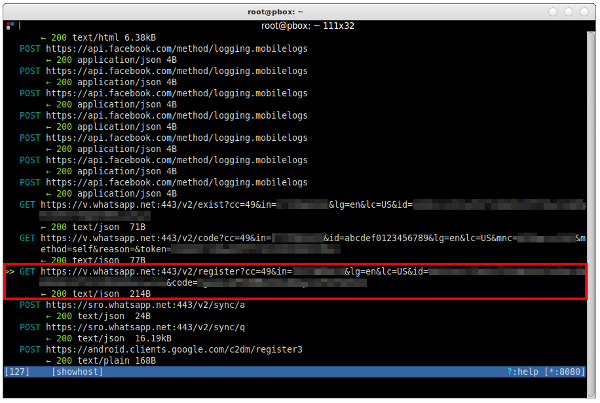
If everything went according to plan, you should now see a couple of requests to the domain v.whatsapp.net — particularly something like this:
- https://v.whatsapp.net:443/v2/exist?cc=49&in=<<your login>>&…
- https://v.whatsapp.net:443/v2/code?cc=49&in=<<your login>>&…
- https://v.whatsapp.net:443/v2/register?cc=49&in=<<your login>>&…
Mitmproxy should show a screen that looks very similar to this:
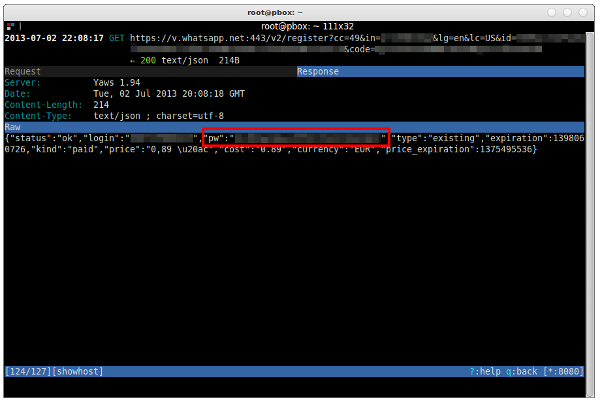
You can find your WhatsApp account password in the last of those three requests (https://v.whatsapp.net:443/v2/register?…). Use the arrow keys to navigate to this entry and hit the RETURN key. Then hit TAB to switch to the ‘Response’ overview. And there it is — a JSON reply of the WhatsApp server as a response to the register-request. Your WhatsApp username is indicated by the “login” key, your password by the “pw” key.
Copy the password and save the conversation with the WhatsApp server by using mitmproxy’s save function: Go back to the main screen by hitting q, then hit s and enter a file name (e.g. /home/user/WhatsApp-password.mitmproxy). You can later load this conversation with L.
2.5. Use the password in scripts
So what’s the password good for? You can use this password in scripts or web applications to send and receive WhatsApp messages. I use the PHP framework WhatsAPI to receive notifications from my server and HTPC. As of now, I only use it to receive alerts and warnings from my monitoring service (Nagios) and to get notifications from my podcast download scripts.
If you’re interested to see how this works, please check out my blog post about how to send and receive WhatsApp messages using PHP.
3. What this cannot do
One additional comment to what this method does not achieve: Unfortunately, the above described method does not allow reading or altering WhatsApp messages sent from your phone or received by your phone. The WhatsApp application only performs administrative tasks over HTTPS (such as status changes or the login). It does not, however, send or receive messages over HTTPS.
Instead, WhatsApp uses a derivate of the Jabber/XMPP protocol to communicate. It communicates on port 5222 over a secure TLS/SSL connection. In theory, and probably also in practice, these connections can also be intercepted like described above. However, I have at the moment not found any transparent TLS/SSL proxy tool for non-HTTP(S) connections/traffic. As soon as I find one, I’ll write another blog post about it. Please let me know if you have any suggestions.
Update (July 2013): WhatsApp does not use TLS/SSL on port 5222 as I wrongfully stated above. Instead, it uses its own proprietary protocol to exchange and encrypt messages. That makes sniffing into the connection a little more cumbersome, because simply listening to the socket is not enough. While the individual WhatsApp messages (“nodes”) can be extracted using tcpdump (try: tcpdump -X -vv -i eth0 'port 5222'), the results are quite disappointing at first:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
20:03:46.645026 IP (tos 0x0, ttl 50, id 42975, offset 0, flags [DF], proto TCP (6), length 267) 50.22.231.44-static.reverse.softlayer.com.xmpp-client > pbox.fritz.box.38975: Flags [P.], cksum 0xc9a7 (correct), seq 143:358, ack 124, win 514, options [nop,nop,TS val 924424164 ecr 631853177], length 215 0x0000: 4500 010b a7df 4000 3206 1406 3216 e72c E.....@.2...2.., 0x0010: c0a8 b21c 1466 983f ae43 0976 fdc2 b59d .....f.?.C.v.... 0x0020: 8018 0202 c9a7 0000 0101 080a 3719 97e4 ............7... 0x0030: 25a9 5079 8000 5e54 18d1 a86c 8e70 cf13 %.Py..^T...l.p.. 0x0040: 290f 3a28 6add b8f6 f8e3 10d7 7bc5 f965 ).:(j.......{..e 0x0050: b672 fe25 fdb8 4730 ce3a dcbe b040 0df4 .r.%..G0.:...@.. 0x0060: 84c4 581d d8df 996e 50d5 7f12 b6bf 24f7 ..X....nP.....$. 0x0070: 0d72 f46d 704d cb21 7a56 2032 bc1a e15c .r.mpM.!zV.2... 0x0080: 88db d754 e3a3 4aa7 e7dc a2ad d2f4 2841 ...T..J.......(A 0x0090: f3b8 d52c 6180 005e 524b 1573 757d 2095 ...,a..^RK.su}.. 0x00a0: 5f64 28da 3518 1e37 1a07 0f41 265a 867c _d(.5..7...A&Z.| 0x00b0: f016 6e0e 114b 73f2 329f d1b2 b17b dc6f ..n..Ks.2....{.o 0x00c0: 1d16 0b62 194e 9d26 b5cd d5d1 321e b033 ...b.N.&....2..3 0x00d0: ce40 8afe e6c6 79bf 4ada 5149 f29a be13 .@....y.J.QI.... 0x00e0: 291c 503d 4661 5cb5 047b 2dfe 41f9 5db9 ).P=Fa..{-.A.]. 0x00f0: 6442 0eac 0a8d 8000 1222 6248 7dc9 b7a5 dB......."bH}... 0x0100: 563d 4a9a cafe 42f8 011f ee V=J...B.... |
The actual message starts right after the TCP header, so in this example after 52 bytes (8000 5e54 18d1 a86c 8e70 …). Each message can contain multiple nodes, each of which has a tag name, and can have attributes and content (data) — much like in XML. However, because XML is chatty, WhatsApp encodes tag names an attributes with a dictionary, so that certain numbers correspond to certain tags. The snippet above is an encrypted and encoded representation of the following XML-tags:
|
1 2 3 4 5 6 |
<message from="49xxxxxxxx@s.whatsapp.net" id="1375004720-28" type="chat" t="1375034628"> <notify xmlns="urn:xmpp:whatsapp" name="Philipp Heckel"></notify> <request xmlns="urn:xmpp:receipts"></request> Hi there! <offline></offline> </message> |
Nodes can be either encrypted or unencrypted: In an initial “handshake” with the WhatsApp server, the client is authenticated using its username and password (see above). After that, the server provides a challenge which — in combination with the password — is used to encrypt the rest of the communication. The actual encryption is based on a RC4 cipher with 256-bit key size, and the key is derived from the password and the challenge (as a salt) using PBKDF2.
All of these things make it more complex to sniff messages from the wire. However, the guys of WhatsAPI already successfully implemented this protocol, so that a lot of their code can be reused to read WhatsApp messages off the network interface.
I am currently working on a script to do just that. My current approach is to use tcpdump to listen to eth0 and pipe the output to a PHP script that parses the TCP packets and uses WhatsAPI to decode/decrypt the communication. Not the most elegant solution, but so far it works quite well. I will update this post as soon as I have something worth sharing.



I was wondering how this would work on an iPhone as per the article’s title – especially with adding the mitmproxy CA certificate? Could you please elaborate on this?
Hi there, I unfortunately do not own an iPhone or iPad, so I cannot test it I’m afraid.
However, check out this blog post: http://offensivecoder.com/2012/06/27/how-to-add-burp-ca-certificate-to-ipad-or-iphone/
It shows in lots of screenshots how to install a CA on an iPhone.
I just did all this.. went through a lot of trouble with getting whatsapp to run on androvm, cause i don’t have a phone.
If i went to websites and stuff in the browser it gets picked up by mitm-proxy but while setting up whatsapp nothing happened..
Did i do something wrong?
never mind
I didn’t change eth0 to br0 in the line for port 443
Here i am again.. now i did it again.. now i dit get 2 v.whatsapp.com links in it.. but non of them is the right one..
the second has method=sms in the line, but i waited for the phonecall..
There’s nothing more.
Any thoughts?
“”And don’t worry, WhatsApp makes a backup copy on its servers and restores all of your messages and conversations once you have re-setup your account.””
This is wrong at least for Android. WhatsApp does not backup messages on its servers. It only backs up the message onto the phone’s storage, and it happens everyday at 4:00 am. You have to manually invoke backup at other times to back up the messages you received after the last 4:00 am backup. Otherwise, when you restore you will not have any of the recent messages received after the last 4:00 am backup. Also the procedure is best done when no one is messaging you.
Hi Adtc,
thank you very much for the correction. I updated it in the post. I have no idea how I could have missed that. I apologize if that has caused you any trouble.
Best
Philipp
Ok I figured it out with IOS and MissVenom. You have to install the self signed whatsapp cert on your device https://github.com/shirioko/MissVenom/blob/master/MissVenom/all.whatsapp.net.pfx (Password: Banana), so it accepts connections from whatsapp through proxy.
Btw. your sample scripts for whatsAPI give errors due to function name changes in whatsAPI.
Regards, Sandra
I saw that they did change the namings of the functions, … Not sure whether to correct that or not. I have no idea how often they change the names :-D
Hey Heckel
Beautiful article.
I’ve been working on the same project.
I’d be happy to hear if you’ve made any progress recovering plaintexts from ciphers.
Just a small correction for your article- RC4 is a PRGA hence you can’t say 256bit encryption. What you probably mean is the key size. Can you tell for sure that it is 256bits?
My work currently focuses on taking yowsup’s code and reading “air” msgs with it. I’ll let you know once I make any progress if you’d like.
Cheers
Hi there,
I wrote a little script that can take TCP packets from the wire and decipher them if the password is known. So I am not exactly attacking the cipher or anything, it’s simply decrypting the ciphertext. Here’s what I’ve got right now — nowhere near finished: http://pastebin.com/Wsj8QrgL
You can use it like this: $ tcpick -X 1 -yH | ./whatsapp_monitor.php
It probably does not work with the current version of WhatsAPI. I’m still on the commit from 30 July 2013 (https://github.com/venomous0x/WhatsAPI/tree/55323fc1177324343825031c4891314d8b570a1c).
Regarding the 256-bit question: WhatsAPI uses 256-bit hardcoded in the rc4.php file:
PDKDF2: https://github.com/venomous0x/WhatsAPI/blob/f2caa156b19a31140e4c4df8c7e9ab0af4406440/src/php/whatsprot.class.php#L1295
RC4 256-bit: https://github.com/venomous0x/WhatsAPI/blob/f2caa156b19a31140e4c4df8c7e9ab0af4406440/src/php/rc4.php#L53
Best regards
Philipp
Hello, first of all thanks you for the paper.
I installed mitmproxy, everthing works fine.. installed certicated , I Can browsing the web by firefox and the android default browser, I can enter to facebook and I can to get the password in text plain by Mitmproxy, It’s great!.. but.:
I stopped whatsapp.
I deleted user data.
I restarted my phone.
ok.
Started Whatsapp, I click on “Agree and Continue”, Then, It ask me my phone number and when I input my number and click “OK” Whatsapp tell me: “You don’t have Internet Conexion, restart you phone and try again”..
Any suggestions?
Hello, I would like to congratulate you for your work, I also have the same problem of Emilia! perhaps a recent update of Whatsapp has made it impossible to sniffing the connection?!?
You guys are trying to decrypt the conversation using the password. But as has been said, the server challenge is used to encrypt/decrypt all the subsequent traffic after the handshake. Therefore why not grabbing the challenge bytes and and use it to decrypt the traffic? (knowing that the challenge bytes are sent in clear at first…)
I guess I’m going to try this…
I am using windows instead of Linux ,Can you please tell me how to know the password of whatsapp ?
Check out MissVenom, as described in section 1.1
Hi Phillipp, I would like to attempt this as a university project for an IT security subject. Is it possible to sniff the password without a full proxy but an actual sniffer (such as Wireshark) instead?
Regards
Hello Javier,
the traffic is SSL-encrypted, so Wireshark won’t display anything but encrypted gibberish. You need a SSL-terminating man-in-the-middle proxy.
Best
Philipp
I followed all steps, mitmproxy, certificate, etc… and I can browse the web by HTTPS but when I start Whatsapp, I click on “Agree and Continue”, Then, It ask me my phone number and when I input my number and click “OK” Whatsapp tell me: “You don’t have Internet Connection, restart you phone and try again”..
Maybe a recent update of Whatsapp is working in a different way… Any suggestions? Thanks!!!
As I said in my updates, if they’re checking fingerprints now, MITM might be impossible, but I haven’t tried it recently.
Well, MissVenom is dead now, or at least dead at github. Maybe a threat from WhatsApp?
Who knows …
hello sir
i did all the above steps
and i see the traffic passes through mitmproxy
but i can’t see whatsapp requests
Hi Philip,
I cannot see any packets from whatsapp while registering.
I tried the password sniffing technique you posted, but I cannot see any entries in mitmproxy like this:
v(dot)whatsapp(dot)net:443/v2/register?cc=49&in=<>&’
Instead during registration I see a packet with the following name:
‘android(dot)clients.google(dot)com/c2dm/register3’
and it has entries like ‘Authorization’ and X-GOOG.USER_AID.
@Akhil: The method described in this post does not work anymore. The registration you’re seeing is your Android, not WhatsApp.
Sr philips.
No speak english. please traduce the spanish
Te hago una pregunta: COMO PUEDO HACER PARA VERIFICAR QUE NUMERO TIENE WHATSAPP Y CUAL NO ? gracias
How will I get the password?
This tutorial does not work anymore?
Thanxs
I have tried to do this on a OSx 10.9.1 but no success. Will there be a how to for Mac ?
hello,
if we need to open up whatsapp on a firewall, what ipaddress ranges and ports do we configure allow in the rule policies?
Do they have a specific range of ip’s to XMPP ports ?
Kind Regards
MZ
how to setting in nagios, can you give me tutorial,
I was wondering if this tutorial still work? If someone can answer. Thank you very much.
Hello.
Can any one provide me step by step procedure in document format ?
because i am not able to perform this on my cell phone.
Thanks
-Lalit
Hi –
Excuse the oversight if this has been answered to or inferred to in this document.
Assuming the user:
a) Already has WhatsApp on their device and is a current user of WhatsApp
b) Remembers their WhatsApp login credentials (username and password),
Would this information they have suffice, or does WhatsApp further encrypts this information, in order to send/Receive WhatsApp messages using the PHP code you have provided?
Again, please excuse the above if already answered, I just seem to find it in the above.
Thanks in advance.
Larry.
I was trying to intercept WhatsApp packages.
I use unrooted Android on my Nexus 4. It went well with unencrypted http packages sent by chrome browser, but when i was trying to intercept WhatsApp packages, app dialog told me that there are some connection problems. It also refused to load google.com, cuz it uses https i think. I generated my own certificate.
I think i m doing something wrong, so I’d use some help. Thanks.
Thanks,
This is a very helpfull article.
I have not send any image ,audio and video
I have use below methods
$w->sendMessageImage($target, “demo/x3.jpg”);
//send video
$w->sendMessageVideo($target, ‘http://LINK_REMOVED/demos/sample-videos/small.mp4’);
//send Audio
$w->sendMessageAudio($target, ‘http://LINK_REMOVED/tech/piano2.wav’);
can i use whatsapp on proxy server
Sir i have linux machine tell me the tutorial for how to sniff password in windows using MisVenom tool
Hello
I need whatsapp bulk messenger version is not mater any one let us one.
Thanks & regards
Amodkumar
How get whatsapp password
Hi Philipp, at the end of your blog you talk about piping ethercap results to a php script that, using whatsapi can decode whatsapp traffic.
Can you explain a litlle bit more how to do this?
Thx
Hello Chano,
I just looked for my PHP script — I literally searched for 15 minutes. I couldn’t find a trace of it anywhere. I’m sorry, but I think it got lost.
The idea was to read the tcpdump/tcpick output, strap off the TCP header data and feel the actual payload to the WhatsApi decode functions for WhatsApp messages. I remember that I ended up using tcpick -yH instead of tcpdump, because it was easier to parse. But the TCP header data was kind of hard to parse. There are probably libraries for that though…
Sorry I can’t be of more help.
Best
Philipp
Its not working as no section in mitmproxy
how to download mitmproxy certificate
Hello,
I made an app that displays your WhatsApp password.
Check it out here https://play.google.com/store/apps/details?id=com.smorra.passwordextractor
Best regards
Strange!
I tried your app “Password Extractor” (wondering what many permission this needs, but I didn’t give internet permission) and checked the password.
It is different from the password which I got through yowsup (on a linux machine), which indeed works, because I use it in pidgin with success.
So either the app is not working and gives a wrong password, or some other thing is wrong.
What could that be?
frank
Hi guys, i was able to install and have it working fine. i can see traffic when i
m using a browser on my iphone, but im no able to have internet connection when using applications. it mean, when i have a fresh installation of whatsapp it say i have no internet connection. just like app store and etc. only browsers are able to find my internet connection. What should i do to have it fixed?Thanks in advance and nice article.
Hi!
I have the same problem as Claudio.
Can anyone help us?
Hi!,
Me too have the same problem as claudio & florent. Is this due to some fake certificate issue?
Hello sir
I am the php developer and implement this whatsapp api for send bulk sms script. but i have an issue. when i register my number with whatsup api then it logout in my device. and when i use in my device (same number) then i again verify my number in my
device. and if i use in my php api then i again register my number with api. Please tell me the solution so not register again and again in api and
device.
Also please tell me that how many sms we send in bulk from bulk.php at a time. and how long time this api runs in future.
Please reply as soon as posible.
Thank you
Saurabh
Hello
Greate your tutorial.
I try to get whatsapp password, with MissVenon and Mitmproxy, but both are not sniffing the calls and in ios device when insert my cellphone number and send does not work too. Does the Whatsapp created recently block to MissVenon?
Please tell me how can i retrive my whatsapp password. i try more and more time but i can’t able to do it. so please help me.
Thanks
i have a little bit knowledge of c#.
Excellent.
I’ve been wondering. Can I receive google email as a whatsapp message? Is this possible?
how can i retrive my whatsapp pass.
i have pwd.
I am C# developer
This is much easier http://www.17educations.com/whatsapp/how-to-get-whatsapp-id-and-password/
How do I delete my pass code from whatsapp apps
Will this still work with the new end-to-end encryption?
Hello,
thank you for a great tutorial! I want to ask, is it possible to somehow redirect WhatsApp’s communication to port 8080? I just want to see a message in mitmdump saying that it doesn’t trust the certificate provided by mitmproxy. I can see this message for all the media files sent as they are sent through http.
how i can to sniff password using chrome console? Or it’s not possible?
Hi Phil, this is really interesting….so I am currently trying to send messages to users on my website via WhatsApp. Placing the message and my phone number as a url parameter in an anchor link works but then they have to click on it to begin a conversation and its also not dynamic at all. but I came across some techniques on your blog and It is amazing! My question is, If I am sending a message to someone, do I still need to fetch my whatsapp password like this tutorial says?
I guess the repo is down
WhatsApp no longer sends password in the register response. They might have moved it to the encrypted xmpp messages. WhatsApp is using certificate pinning to circumvent mitm. You can still bypass certificate pinning by using Xposed module called SSLUnpinning 2.0 in xposed framework.